Using Cisco Packet Tracer To Design A Network Setup
Today, I thought of using a Cisco packet tracer to design a star topology after I tried designing a tree topology but failed to understand the correct form because tree topology is an advanced extension form of star topology; here is my own form of star topology. After thorough research and videos on the right way to do it.
Screenshot taken by me
I will be more focused on developing a Standard Star Topology Network. Every organization has a network setup. Most of us think a network is just about a wired network and a wireless network, but it goes deeper than this, especially when trying to set up an organization network to prevent vulnerabilities or breaches in the network.
Presently, technology keeps on advancing day by day, and most people develop tools for wifi hacks or potential threats to networks. Every organization prefers to save data and personal information online or on the computer, and when there is a breach, it is easier for hackers to gain access to this information; this is why most organizations prefer to build up a standard network setup.

Screenshot taken by me
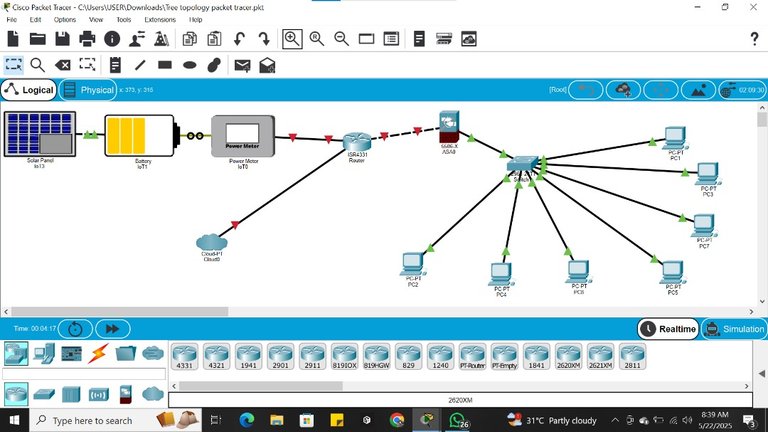
There are several types of network setups, but I will be trying to design a star topology with my Cisco packet tracer. A star topology is a wired connection, whereby all devices are physically connected. This will be my first network setup ever.
Most companies often need a standard network setup in other to communicate with their client perfectly and run a smooth operation of the company.
Screenshot taken by me
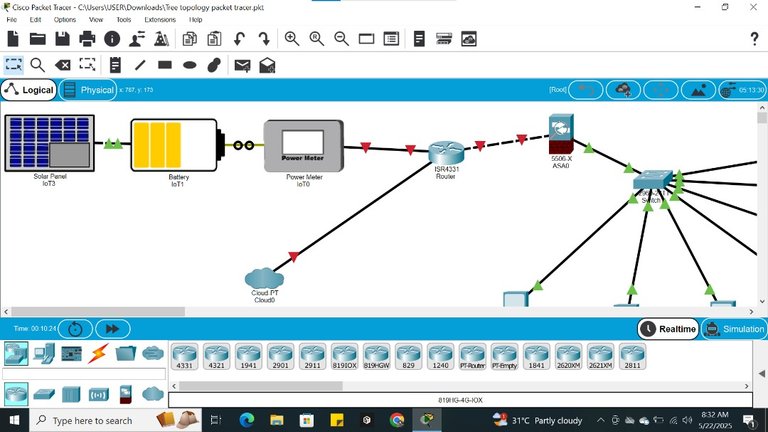
Under Star topology, the Central node connects to all the computers, and the firewall protects the central node against breaches, we have the cloud where we store data and information, and we also have a battery that protects the central node and hub from switching off during any power outage, while the solar powers the battery.
There are things we must take note of about the topologies of a network, all of the network topologies including star topology, tree topology, bus topology and several others are good but they all have their advantages and demerits, some can be easily breached by hackers while some can't be easily breached this is why company take not of topologies of network to use.
Star topology can be regarded as the safest because it is majorly a wired connection, but it has its own disadvantage, which is that when there is a power outage in the network, it all goes off. This is why they prefer using solar and inverter batteries to protect,t it. If not, they lose connection. Another reason Star Topology is safe is that an outsider can't access the network unless he connects the network ethernet cable to his system or computer.
All devices in a star topology connect to the central hub; devices not connected can't be used or accessed. Most Banks in Nigeria use the Star topology network for their bank works on their computer because if there is any breach, it is traceable to the system. After all, it is a completely wired connection, and they also create a wireless connection for random use.
Star topology is the safest and the best against hackers, just that it requires a complete Ethernet cable connection for the system to perform perfectly.
I am specifically more focused on Penetration testing and threat intelligence. I just decided to give the Cisco packet tracer a trial to develop a network set-up, but I just wanted to try my skills on this, If you notice anything wrong in my diagram, we can talk about it.
THANK YOU FOR READING MY POST
Posted Using INLEO