Keeping Secrets - Gitleaks and Github

Vote for Brianoflondon's Witness KeyChain or HiveSigner
Support Proposal 342 on PeakD
This is a value for value post: see the explanation in the footer.
Warning: technical blog post follows for coders
I just did something I should have done years ago. I installed a pre-commit scanner in my workflow to check before I upload anything to github that I haven't divulged any secrets.
The mistake
I haven't made this mistake yet, but that's the point about fixing security stuff: far better to do it before you make the mistake.
Let's say I have a file like this with some keys in it. They're just random keys, generated with my own v4v.app signup for Hive link but lets assume they're the keys to my server's Hive account.
Hive Username: koiuoiulkj
Owner Key: 5JB6MK6CHipcYCmZtFbBVV19qbAXaFMZXYcRLEHKa5Hndj2AYkG
Active Key: 5JFFgEhSRoso1pEFRFDtzrN3rjhLqPJuYgejiGfD9FroMLZNRv9
Posting Key: 5JRpckhZgBSN2SxZJzBQAAdMgffoWXrwF6BTtqpz7mw7NZrkCP5
Memo Key: 5KMNg6mvMGBNZxUWQVwczD2x6TXJnHCQ3PvqE5hQuWqmB5rm5ts
Backup (Master) Password: bsKCHNClqvDpTb1QMd17LaQi79xygJjR
It's easy as you like to put those in a file and accidentally add it to github. At least here on Hive, if you notice such a catastrophic error, you can change your keys but it's a big hassle.
Pre-commit hooks
The solution which I should have put in place years ago is to use something called a "pre-commit hook" to scan anything I try to send to Github before I upload it and make it public.
With the help of Grok I decided to use Gitleaks, this is what Grok has to say about it.
Gitleaks
Reputation: Highly regarded in the security and DevOps communities for its speed, ease of use, and Git-focused approach.
Strengths:
Specifically designed for scanning Git repositories, making it excellent for catching secrets in commit history and pre-commit hooks.
Fast and lightweight, with a simple setup.
Broad rule set covering common secret patterns (e.g., AWS keys, JWTs, private keys).
Active community and frequent updates (e.g., latest release in 2025).
Integrates seamlessly with CI/CD pipelines and pre-commit frameworks.
Community & Adoption: Widely used by security professionals and developers, with over 16k GitHub stars (as of last data). Popular in enterprise and open-source projects for its reliability.
Criticism: Can produce false positives without fine-tuning, and its focus on Git means it’s less flexible for non-Git use cases.
I followed the steps on the Gitleaks github page to install and voila it's working.
What happens?
So when I try to post that file to Github now, this is what I get:
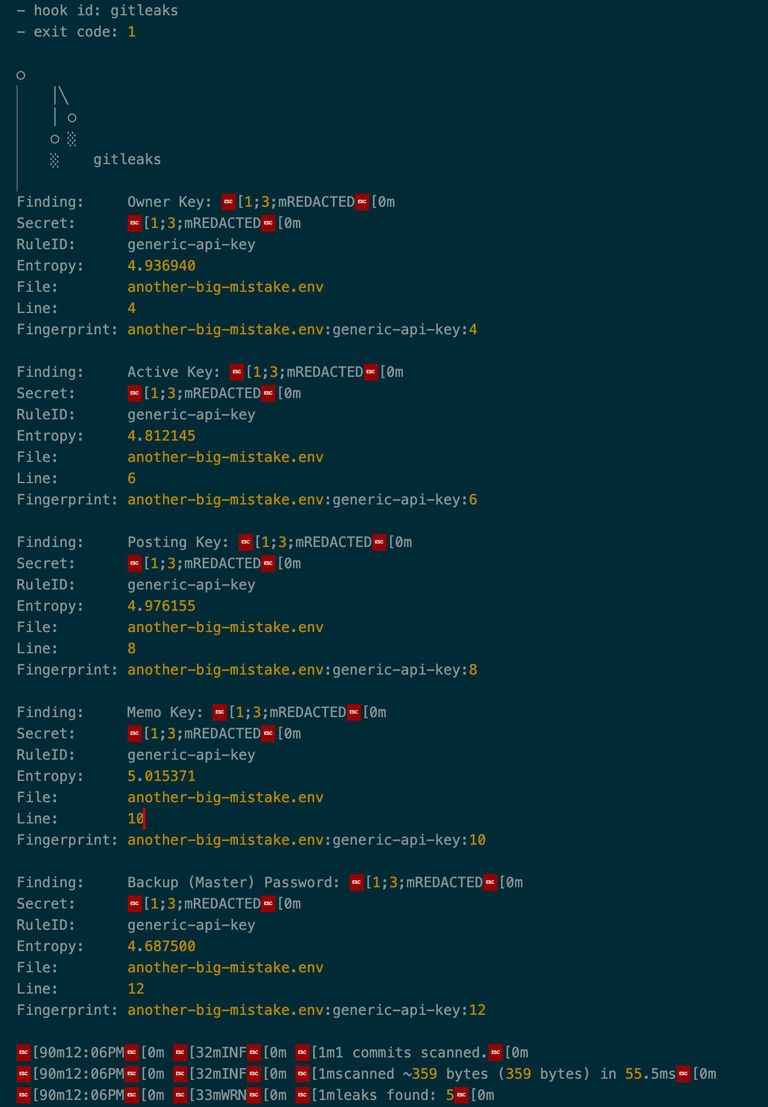
I deliberately tested with Hive keys and without doing any further setup.
Honestly I feel really dumb for working this long without setting this up.
Value for Value
For the last few months while building @v4vapp I was generously supported by the DHF. Going forward I have a much more modest support which covers direct server costs and a little of my time.
If you appreciate the work I do on and around Hive, you can express this directly: upvoting posts on Hive is great. Also consider a direct donation (there's a Tip button on Hive or a Lightning Address) on all my posts.


Support Proposal 342 on PeakD
Support Proposal 342 with Hivesigner
Support Proposal 342 on Ecency
Vote for Brianoflondon's Witness KeyChain or HiveSigner

So this Tool recognizes any private keys within a written code and gives you feedback about it BEFORE you upload the code? How does it recognize some random Numbers and letters being a secret key? Is that AI power of learning to recognize patterns?
Do you have to train rhe tool of recognizing certain secrets? For example how does it distinguish between a number within a code being just a number form being someones private phone number or Bank Account number that should remain secret?
I think its mostly a bunch of regex expressions but I haven't looked into exactly (I really will) but right out of the box, it detected that file but for example in my test folder the following:
Didn't raise any alarm bells. As you can see the ####'s are there so that when I'm editing that file i know not to put any secrets in it!
I just now tried replacing the hive keys
somepostingkeyetc with real (looking) randomly generated keys and sure enough it blocked upload. Perfect. I'm sure there is a way I can flag stuff as safe for specific testing reasons but this is working just how I want it to.Very cool. 👍🏻
Reading this I am so sure that you must have spent tons and tons of hours researching and building this. I am so sure that it is not something so easy but you devote your time and energy to this which is really a great job you are doing
Thanks for been an inspiration
Doesn't really work for me. It's probably looking for some keywords like
passwordorkeyfollowed by what it guesses to be the secret. Simply removing those keywords but leaving the actual keys from the example file above makes it a false negative.I'm absolutely not thinking of relying on this and becoming dumb. I suspect it's better with more common things like API keys which it will have seen more than Hive keys.
Maybe this is of interest to you Brian:
https://x.com/Boltzhq/status/1873778286947688831
Congratulations @brianoflondon! You received a personal badge!
Participate in the next Power Up month to get another one!
You can view your badges on your board and compare yourself to others in the Ranking
Check out our last posts:
Congratulations @brianoflondon! You received a personal badge!
Wait until the end of Power Up Day to find out the size of your Power-Bee.
May the Hive Power be with you!
You can view your badges on your board and compare yourself to others in the Ranking
Check out our last posts:
Congratulations @brianoflondon! You received a personal badge!
See you at the next Power Up day to see if you will repeat this feat.
May the Hive Power be with you!
You can view your badges on your board and compare yourself to others in the Ranking
Check out our last posts:
A Wake-Up Call: Accountability and Redemption in the Hive Ecosystem
To those who believe their actions on the Hive blockchain go unnoticed, it’s time to confront the truth. The power you think you wield through downvotes, vote farming, and manipulation is an illusion. True strength lies in doing what’s right, not in exploiting systems for personal gain or silencing others out of fear.
1. The Illusion of Power Through Exploitation
If you’re downvoting critics, running coordinated farms, or hoarding influence to control rewards, ask yourself: What does this say about your character? Manipulating Hive’s reward system doesn’t make you powerful—it exposes vulnerabilities. It shows a reliance on unethical tactics to feel significant in a space that was meant to empower everyone equally.
But here’s the reality: these actions won’t bring lasting satisfaction. At night, when you’re alone with your thoughts, do you truly believe what you’re doing is right? Regret has a way of lingering, and no amount of HIVE tokens can silence the voice inside telling you there’s a better path.
2. The Ripple Effect of Your Actions
Your choices don’t just harm Hive—they affect the people around you. Your online friends may follow along now, but loyalty built on shaky foundations crumbles quickly. And what about your family? Do they understand how much energy you pour into behaviors that ultimately hurt others and yourself?
Every action has consequences, and the deeper you dig, the harder it becomes to climb out. You’re not just harming Hive—you’re pulling those close to you into a cycle of negativity and regret. Is it worth it?
3. Change Before It’s Too Late
The Bilpcoin team isn’t here to attack individuals—we’re here to spark change. We’ve seen the evidence, and we know the impact of manipulative practices. But we also believe in redemption. There’s still time to step back, reflect, and choose a different path.
Ask yourself:
Hive deserves better. So do you.
4. Strength Lies in Doing What’s Right
Real power comes from integrity, not manipulation. Instead of focusing on how many tokens you can farm or how many users you can silence, consider how you can add value to the ecosystem. Create meaningful content, support genuine contributors, and advocate for reforms that benefit everyone—not just a select few.
If you continue down your current path, remember this: you are being watched. Many stay silent, but they see everything. Blockchain data doesn’t lie, and accountability always comes knocking—whether today, tomorrow, or years from now.
5. A Final Plea: Fix What Needs Fixing
It’s never too late to change course. Stop the farming, stop the toxicity, and start contributing to Hive in ways that uplift rather than tear down. If you’re struggling with why you’ve chosen this path, take a moment to reflect. Seek help if needed—there’s no shame in admitting you’ve lost your way.
The Hive community is watching, waiting, and hoping for positive change. Will you rise to the occasion, or will you let regret define your journey? The choice is yours.
From the Bilpcoin Team: We’re committed to helping Hive thrive by exposing the truth and fostering transparency. Let’s work together to build a stronger, fairer ecosystem—one where everyone has a chance to succeed.
What will your next move be?
Addressing the Downvote Issue on Hive: It’s Time for Real Change
Marky Mark Stop the manipulation game Lady Zaza Bpc AI Music
Let’s cut through the noise and address one of the most pressing issues holding Hive back from reaching its full potential: abusive downvotes. The Bipcoin team has consistently exposed the systemic problems that stifle growth on this platform, yet little to no action has been taken. If Hive is to thrive, we must confront these challenges head-on instead of engaging in empty discussions that lead nowhere.
Hive cannot grow if nothing changes. How can new users and smaller creators flourish when they are constantly suppressed by those who exploit the system? Many so-called “whales” contribute nothing meaningful to the ecosystem—instead, they focus solely on farming rewards through manipulative tactics like mass self-voting, spam content, or coordinated downvoting campaigns. These actions discourage genuine participation and erode trust within the community.
Blockchain transactions don’t lie. We’ve seen firsthand the shady methods used to game the system—whether it’s creating alt accounts to amplify votes, orchestrating downvote brigades, or hoarding influence without giving back to the network. Why does this behavior continue unchecked? Talk is cheap. Actions speak louder than words, and until concrete steps are taken to address these abuses, Hive will struggle to move forward.
We have repeatedly presented evidence of these practices, not to divide but to demand accountability. The truth is out there for anyone willing to look at the data. Yet, despite our efforts, the cycle persists. Today, we’re asking again: Can we finally talk about the real issues plaguing Hive? And more importantly, can we take decisive action to protect the integrity of this platform?
Do not let bullies destroy what makes Hive special. Abuse of power through downvotes and manipulation harms everyone—creators, curators, and the community as a whole. It’s time to fight back against these toxic practices and create an environment where all voices can be heard and rewarded fairly.
The Bipcoin team remains committed to exposing the truth and advocating for meaningful change. But we can’t do it alone. Together, let’s push for solutions that ensure Hive becomes a place of opportunity, fairness, and growth—for everyone.
Enough talk. Let’s see action.
Every curation reward from @buildawhale’s bot votes:
The blockchain doesn’t forget—your actions are permanently recorded. So, enjoy your scam farm snacks now, because karma always delivers the bill.
https://peakd.com/@buildawhale/comments
https://peakd.com/@buildawhale/activities
Staked HIVE
More
Also known as HP or Hive Power. Powers governance, voting and rewards. Increases at an APR of approximately: ~13.07%
An unstake (power down) is scheduled to happen in 5 days (~4,742.795 HIVE, remaining 12 weeks)
61,991.841
Tot: 2,404,544.432
Delegated HIVE
Staked tokens delegated between users.
+2,342,552.591
Details
HP Delegations
RC Delegations
Delegated: 0 HP
Search
No outgoing delegations
Received: 2,342,553 HP
@blocktrades 2,342,494 HP Aug 16, 2020
@nwjordan 24 HP May 27, 2018
We’ve exposed the truth repeatedly with ironclad evidence:
@themarkymark’s $2.4M scam farm.
@buildawhale’s daily grift.
@jacobtothe’s downvote army.
Downvote Army: Silencing truth-tellers like Bilpcoin.
Reward Yourself: Collecting daily paychecks from @buildawhale.
https://hive.blog/hive-124838/@themarkymark/re-jacobtothe-st6rk4
https://hive.blog/hive-167922/@usainvote/re-buildawhale-s6knpb
https://peakd.com/hive-124838/@bpcvoter1/st7wu1
https://peakd.com/hive-126152/@bpcvoter1/jacobtothe-you-re-not-god-no-matter-how-much-you-try-to-act-like-it-you-can-say-what-you-want-but-the-truth-remains-undeniable
https://peakd.com/hive-163521/@bpcvoter3/jacobtothe-this-was-way-over-rewarded-and-we-need-to-call-it-out-you-made-significant-rewards-from-a-post-that-was-created-using
https://peakd.com/hive-126152/@bpcvoter3/jacobtothe-let-s-address-the-core-issue-here-facts-speak-louder-than-rhetoric-we-ve-presented-verifiable-evidence-that
https://peakd.com/hive-126152/@bpcvoter3/think-carefully-about-your-next-move-because-this-issue-is-bigger-than-any-one-of-us-the-downvote-abuse-scamming-and-farming-by
https://hive.blog/hive-180505/@jacobtothe/re-denmarkguy-st9f4w
https://hive.blog/hive-124838/@themarkymark/re-peaksnaps-starqg
https://hive.blog/hive-167922/@darknightlive/re-bpcvoter2-bpc-dogazz
https://hive.blog/hive-126152/@tobetada/my-first-shitstorm#@azircon/re-tobetada-stbswq
https://hive.blog/hive-124838/@acidyo/re-themarkymark-stbthn
https://peakd.com/hive-168088/@bpcvoter3/jacobtothe-it-seems-we-re-going-in-circles-here-so-let-s-clarify-things-once-and-for-all-downvotes-don-t-erase-the-truth-the
https://peakd.com/hive-126152/@bpcvoter3/uwelang-it-seems-you-re-dismissing-the-discussion-without-engaging-with-the-actual-content-that-s-unfortunate-because-the
https://peakd.com/hive-121566/@bpcvoter1/std7q6
https://peakd.com/@uwelang/re-uwelang-stc2c3
https://hive.blog/hive/@themarkymark/what-the-fuck-do-witnesses-do-dk1
https://hive.blog/hive-167922/@usainvote/re-buildawhale-s5tysw
https://hive.blog/hive-124838/@steevc/re-meno-stdsv6
https://hive.blog/life/@crimsonclad/re-oldsoulnewb-sh93a2
You Can't Downvote The Truth Mc Franko Bpc Ai Music
https://hive.blog/hive-126152/@jacobtothe/re-galenkp-stekn4
https://hive.blog/hive-126152/@jacobtothe/re-galenkp-steiss
https://hive.blog/hive-124838/@acidyo/re-web-gnar-stfc6c
https://hive.blog/mallorca/@azircon/re-abh12345-stfbyk
https://hive.blog/hive-167922/@uwelang/hpud-march-back-over-110k-hp
https://hive.blog/burnpost/@buildawhale/1742569802434998164
https://hive.blog/burnpost/@buildawhale/1742656202460243008
https://hive.blog/hive-124838/@themarkymark/re-peaksnaps-sti6pr
https://hive.blog/hive-124838/@themarkymark/re-peaksnaps-stkfjj
https://hive.blog/burnpost/@buildawhale/1742742602124717444
https://hive.blog/burnpost/@themarkymark/re-kgakakillerg-stm4vv
https://hive.blog/hive-124838/@themarkymark/re-snap-container-1742690880-20250324t025303z
https://hive.blog/donation/@crimsonclad/re-nampgf-sti0nf
https://hive.blog/hive-148441/@azircon/re-curamax-stk5vq
https://hive.blog/hive-funded/@acidyo/re-alex-rourke-stluzc
https://hive.blog/hive-167922/@theycallmedan/re-finpulse-4gnm7o8h
https://hive.blog/hive-144400/@blocktrades/st110u
https://hive.blog/hive-148441/@usainvote/re-curamax-stly39
https://hive.blog/hive-167922/@usainvote/re-buildawhale-s75mua
https://hive.blog/burnpost/@buildawhale/1742829002430606097
https://peakd.com/hive-167922/@bpcvoter1/themarkymark-big-bad-marky-huh-lol-you-re-more-of-a-joke-than-anything-else-we-ve-exposed-your-actions-repeatedly-your-scamming
https://hive.blog/3dprinting/@themarkymark/meet-frank-ajt
https://hive.blog/burnpost/@buildawhale/1742483402094376205#@buildawhale/re-1742483402094376205-20250320t151108z
https://hive.blog/curation/@azircon/re-acidyo-stn05u
https://hive.blog/curation/@themarkymark/re-azircon-sto5b9
https://hive.blog/curation/@themarkymark/re-azircon-sto57d
https://hive.blog/curation/@themarkymark/re-meno-sto4ua
https://hive.blog/hive-124838/@themarkymark/re-snap-container-1742825520-20250325t020936z
https://hive.blog/hive-150342/@steevc/re-alessandrawhite-2025325t91011757z
https://hive.blog/curation/@themarkymark/re-meno-stodj2
https://hive.blog/curation/@themarkymark/re-meno-stod08
https://hive.blog/hive-13323/@moeknows/re-azircon-stnrc3
https://hive.blog/hive-112018/@jacobtothe/re-dynamicrypto-sto8ak
https://hive.blog/hive-13323/@azircon/re-moeknows-stofom
https://hive.blog/burnpost/@buildawhale/1742915402155436654
https://hive.blog/hive-13323/@azircon/re-moeknows-stoq3o
https://hive.blog/hive-13323/@bpcvoter1/stos6z
https://hive.blog/technology/@themarkymark/re-kgakakillerg-stpzn7
https://hive.blog/hive-124838/@themarkymark/re-niallon11-stpzmi
https://hive.blog/hive-124838/@themarkymark/re-peaksnaps-stpx2t
https://hive.blog/hive-13323/@azircon/re-moeknows-stov0c
https://hive.blog/burnpost/@buildawhale/1743001802743637765
https://hive.blog/hive-124838/@meno/re-themarkymark-stqdnp
https://hive.blog/hive/@acidyo/hive-curation-a-response-to-a-post-about-my-previous-video
https://hive.blog/hive-124838/@themarkymark/re-meno-stqt8y
https://hive.blog/burnpost/@buildawhale/1743088202593656720
https://peakd.com/@bpcvoter1/to-the-hive-community-and-all-those-watching-our-journey
https://hive.blog/hive-124838/@themarkymark/re-snap-container-1743079680-20250328t095442z
https://hive.blog/hive/@acidyo/re-freecompliments-strts3
https://hive.blog/hive-124838/@themarkymark/re-peaksnaps-sttukk
https://hive.blog/hive-124838/@anderssinho/re-themarkymark-stu0qr
https://hive.blog/hive-124838/@oldsoulnewb/re-themarkymark-stu1t3
https://hive.blog/hive-124838/@acidyo/re-themarkymark-stu3fk
https://hive.blog/hive-124838/@wiseagent/re-themarkymark-stu6fz
https://hive.blog/hive-124838/@stayoutoftherz/re-themarkymark-stu6r7
https://hive.blog/hive-124838/@themarkymark/re-peaksnaps-stufv1
https://hive.blog/hive-124838/@themarkymark/re-godfish-stujq7
https://hive.blog/hive-124838/@themarkymark/re-coininstant-stugcr
https://hive.blog/hive-124838/@themarkymark/re-snap-container-1743183360-20250329t130534z
https://peakd.com/hive-167922/@bpcvoter3/exposing-hive-s-hidden-manipulators
STOP #buildawhalescam #buildawhalefarm
https://peakd.com/hive-126152/@bpcvoter3/exposing-the-whales-on-the-hive-blockchain
https://peakd.com/hive-167922/@bpcvoter3/the-hive-unveiled-a-journey-through-shadows-and-light
Stand Together Hive Keni & Mc Franko Bpc Ai Music
https://peakd.com/hive-126152/@bpcvoter3/spaminator-why-the-silence-on-the-buildawhale-scam-farm-the-truth-deserves-action
For more insights into blockchain transparency and accountability, visit Bilpcoin’s Publish0x page.
Wow
@themarkymark & CO The same old tactics are at play—calling people names and telling others to avoid them. LOL. Keep digging, and bring your friends along, because you’ve already exposed enough on your own—not very smart. YOU HAVE LOST ALREADY. WE FIGHT BACK WITH THE TRUTH.
Key Issues to Address:
@buildawhale Wallet:
@usainvote Wallet:
@buildawhale/wallet | @usainvote/wallet
@ipromote Wallet:
Author Rewards: 2,181.16
Curation Rewards: 4,015.61
Staked HIVE (HP): 0.00
Rewards/Stake Co-efficient (KE): NaN
HIVE: 25,203.749
Staked HIVE (HP): 0.000
Delegated HIVE: 0.000
Estimated Account Value: $6,946.68
Recent Activity:
@leovoter Wallet:
Author Rewards: 194.75
Curation Rewards: 193.88
Staked HIVE (HP): 0.00
Rewards/Stake Co-efficient (KE): 388,632.00 (Suspiciously High)
HIVE: 0.000
Staked HIVE (HP): 0.001
Total: 16.551
Delegated HIVE: +16.550
Recent Activity:
@abide Wallet:
Recent Activity:
@proposalalert Wallet:
Recent Activity:
@stemgeeks Wallet:
Recent Activity:
@theycallmemarky Wallet:
Recent Activity:
@apeminingclub Wallet:
Recent Activity:
Scheduled unstake (power down): ~2.351 HIVE (in 4 days, remaining 7 weeks)
Total Staked HIVE: 1,292.019
Delegated HIVE: +1,261.508
Withdraw vesting from @apeminingclub to @blockheadgames 2.348 HIVE (10 days ago)
Claim rewards: 0.290 HP (10 days ago)
@blockheadgames Wallet:
Recent Activity:
@empoderat Wallet:
Recent Activity:
@gogreenbuddy Wallet:
Recent Activity:
@rollingbones Wallet:
Recent Activity:
We only expose what is already on the Hive Blockchain. The data speaks for itself, as we keep telling @themarkymark & Co—all they need to do is STOP.
SO PLEASE STOP. It’s time to do the right thing for Hive and its community. Why not just power down and go? Let Hive be free—you add nothing to Hive.
THOSE WHO ARE WATCHING—THIS COULD HAPPEN TO YOU.
PLEASE STOP.
Hive Community: Do You Believe Words or Blockchain Transactions? LOL
SPEAK UP. MAKE NOISE. TAKE A STAND.
Key Issues That Demand Immediate Attention:
The problems are glaring, undeniable, and corrosive to the Hive ecosystem. They must be addressed without delay:
These practices harm not just individual users—they undermine the very foundation of Hive, eroding trust and poisoning the community. Such actions are unethical and outright destructive.
@buildawhale Wallet:
@usainvote Wallet:
@buildawhale/wallet | @usainvote/wallet
@ipromote Wallet:
Author Rewards: 2,181.16
Curation Rewards: 4,015.61
Staked HIVE (HP): 0.00
Rewards/Stake Co-efficient (KE): NaN
HIVE: 25,203.749
Staked HIVE (HP): 0.000
Delegated HIVE: 0.000
Estimated Account Value: $6,946.68
Recent Activity:
@leovoter Wallet:
Author Rewards: 194.75
Curation Rewards: 193.88
Staked HIVE (HP): 0.00
Rewards/Stake Co-efficient (KE): 388,632.00 (Suspiciously High)
HIVE: 0.000
Staked HIVE (HP): 0.001
Total: 16.551
Delegated HIVE: +16.550
Recent Activity:
@abide Wallet:
Recent Activity:
@proposalalert Wallet:
Recent Activity:
@stemgeeks Wallet:
Recent Activity:
@theycallmemarky Wallet:
Recent Activity:
@apeminingclub Wallet:
Recent Activity:
Scheduled unstake (power down): ~2.351 HIVE (in 4 days, remaining 7 weeks)
Total Staked HIVE: 1,292.019
Delegated HIVE: +1,261.508
Withdraw vesting from @apeminingclub to @blockheadgames 2.348 HIVE (10 days ago)
Claim rewards: 0.290 HP (10 days ago)
@blockheadgames Wallet:
Recent Activity:
@empoderat Wallet:
Recent Activity:
@gogreenbuddy Wallet:
Recent Activity:
@rollingbones Wallet:
Recent Activity:
The blockchain data tells the story plainly and clearly. We are not fabricating these claims; we are merely presenting what is already visible for all to see. As we’ve repeatedly urged @themarkymark & Co—the solution is simple: STOP.
SO PLEASE STOP. It’s time to do what’s right for Hive and its community. Why cling to practices that harm others? Power down, step away, and let Hive thrive as it was meant to. You bring nothing positive to this ecosystem.
THOSE WHO ARE WATCHING—THIS COULD HAPPEN TO YOU.
PLEASE STOP.
@themarkymark, Can You Explain Why the Bilpcoin Team’s Accounts Are on Your Blacklist?
@themarkymark We understand you’re a fan of data—so are we. After all, data is king, and when it comes to blockchain, transactions don’t lie and can’t be changed.
@buildawhale’s daily grift
@themarkymark’s 2.4 Hive Power scam farm
For more insights into blockchain transparency and accountability, visit Bilpcoin’s Publish0x page.
https://peakd.com/hive-126152/@bpcvoter1/addressing-concerns-about-hive-s-growth-and-community-dynamics
https://peakd.com/hive-133987/@bpcvoter3/isn-t-it-funny-how-themarkymark-and-co-are-suddenly-talking-about-ke-levels-on-hive-well-look-what-we-found-some-of-the-accounts
https://peakd.com/hive-178265/@bpcvoter1/how-can-we-take-someone-seriously-when-they-have-been-exposed-through-clear-evidence-blockchain-transactions-and-data-and-then